AWS Systems Manager (SSM) is a service that allows you to manage resources on AWS, including instances, VMs, containers, and services, from a central location. It provides capabilities for configuration management, automation, and security management, simplifying operational tasks and improving efficiency in managing AWS infrastructure.
This articles covers configuring SSH tunnelling via AWS SSM. See Secure Data Transfer with SSH Tunnelling for a general setup.
To set up SSH tunnelling through AWS SSM, see the following sections.
Prerequisites
To set up SSH tunneling through AWS SSM in Dataddo, ensure that
- You have an AWS EC2 instance that acts as an SSH bastion server.
- The bastion server accepts incoming SSH connections from Dataddo IPs.
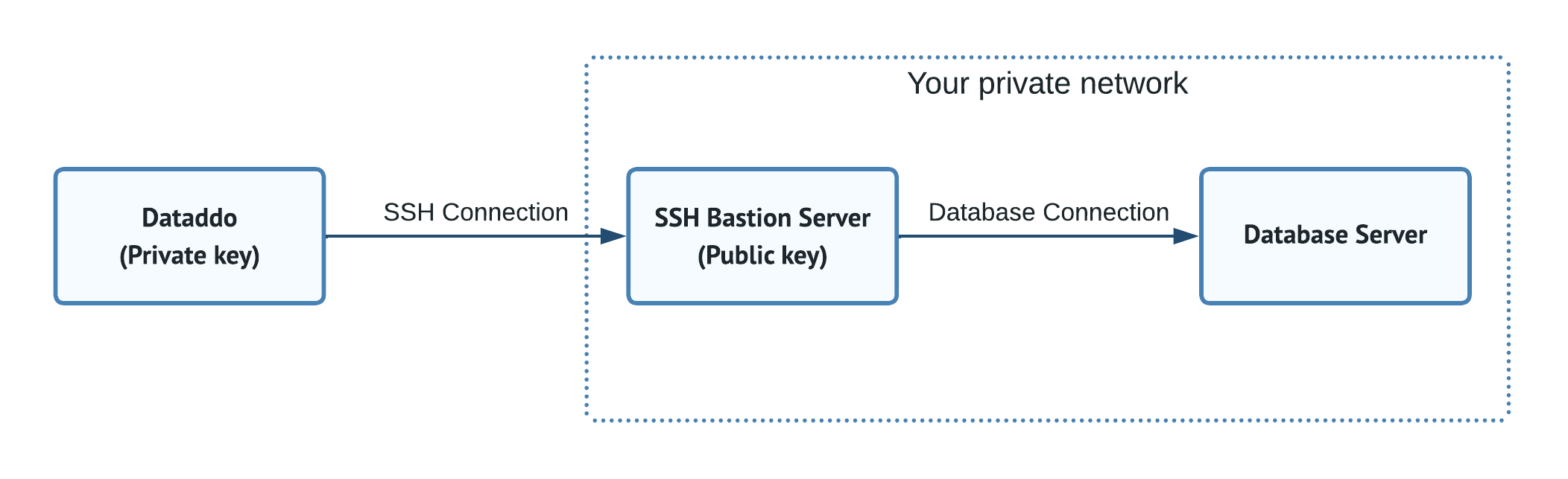
You can refer to the architecture as illustrated in the schema below.
Create and Set up a Bastion Host
Create a Bastion Host
Create a new instance to be a bastion host, or configure your existing one.
- Go to your Amazon EC2 console and click on Launch instance.
- Name your instance and select the following:
- Application and OS Images: Select a minimal and secure Amazon Machine Image (AMI), such as Amazon Linux 2 with a pre-installed SSM Agent.
- Instance type: Choose a minimal instance type (e.g.,
t3.microort3a.micro). - Key pair (login): Click on Create new key pair. Name it and select RSA type and
.pemkey file format. A key will download automatically to your device which you will later upload to Dataddo.
- For Network settings, make sure Allow SSH traffic from box is checked and select Custom. To allows SSH traffic from Dataddo, add all Dataddo IPs (https://docs.dataddo.com/docs/network-acl) using CIDR notation as individual rules.
- Launch your instance.
Integrate Bastion Host with AWS SSM
- In your AWS console, use the search bar to navigate to IAM service.
- Go to Roles and click on Create role.
- For Use case, select EC2 and click on Next.
- On the Set permissions step, look for the
AmazonSSMManagedInstanceCorepolicy and add it (check the box on the left). This role will enable the bastion host to communicate with AWS SSM. - Name the role, review, and add it.
Now, attach this IAM role to the bastion host for proper SSM functionality.
- In your EC2 dashboard, navigate to Instances and select the bastion host instance.
- In the top-right, click on Actions, select Security and click on Modify IAM role.
- Select your newly created role with the
AmazonSSMManagedInstanceCorepolicy and click on Update IAM role.
Make sure to connect your database to the instance.
Authentication Using a Public/Private Key Pair
We recommend using a public and private key pair for authentication. While password-based authentication is an option, it's less secure and not recommended. As illustrated in the schema above, ensure
- The private key is provided to Dataddo, and
- The public key is automatically assigned to the SSH bastion server.
- Go to the Security page and navigate to the Certificates tab.
- Click on Add Certificate.
- Name your certificate.
- For certificate type, select RSA Private Key
- Upload your private key.
- Save your certificate.
Generate a New Public/Private Key Pair
Alternatively, Dataddo can generate a public/private key pair for you. In this scenario, you only need to ensure that the public key is uploaded to your SSH Bastion Server. For this option, please contact us.
Configuring SSH Tunnel to Data Destination
Dataddo supports SSH tunneling for a variety of AWS systems, including, but not limited to, Redshift, SQL Server, MySQL or Postgres.
To establish a connection via an SSH tunnel, follow these steps:
- Navigate to Authorizers and click on Authorize New Service to select a service or system of your choice (e.g. MySQL, Postgres, Redshift ...).
- Fill in the standard database connection details.
- Choose Yes for the Use SSH tunnel field.
- Input the necessary information for your SSH bastion server:
- SSH Server IP or Hostname: Enter the IP address of your SSH server. Ensure your firewall settings permit incoming connections from Dataddo IPs.
- SSH Server Port: Specify the port for the SSH connection (the default is usually 22).
- SSH Server Username: Provide the username for authentication. The username depends on your AMI. See Amazon's official documentation for list of default usernames.
- SSH Server Password: Leave the field empty and select your certificate instead.
- Certificate: Select the Certificate you uploaded to Dataddo in the previous step.